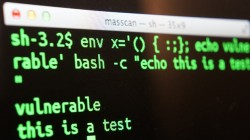
A lot of Linux “bashing” this week, as a Bash bug (one old enough to be able to vote) is causing mayhem for admins all around the world. There’s been a lot of misinformation floating around, mostly being distributed by the mass media, so I thought I would spend a bit of time trying to clear a few things up.
So what is Bash? It’s a shell for Unix/Linux based systems (including OS X). What is a shell? A shell is a command processor, basically something that lets you do everything from listing files and directories, to running programs and piping outputs from them to other programs, to running scripts. When you see hackers in unrealistic Hollywood movies, they’re usually typing a bunch of commands on a black screen with white/green text – then they’re typing on an (most likely made up) shell (with an extremely large font). So just to make it clear, the bug is not called Bash. Bash is the software that has the bug. The bug itself has been called the Bash bug (which I think is where the confusion comes from), although many are calling it by the rather catchy name of Shellshock.
So what is the Shellshock bug? It’s basically a rather silly bug that allows instructions to execute commands to be added to environment variables. It turns a fairly innocuous function that doesn’t really do much into one that can basically do everything.
So instead of running a command which simply set the variable “MyName = Sean”, hackers can instead set the value of the variable “MyName” to be “Sean” plus some command to execute. So instead “MyName = Sean”, they can do “”MyName = Sean; Plus run commands that sends all the password and credit card data on this server to the hacker’s server and then delete all the files on this server”, and this stupid bug will actually allow all of the latter instructions to be executed.
On the surface, a shell bug might not be all that damaging – one would have to already have gained access to the system before you can access the shell. The problem is that many internet-facing parts of a server that runs Bash, including the parts that render web pages and scripts, call upon shells like Bash to perform certain actions, including setting environment variables. This means that, with only a little bit of knowledge, one can potentially execute almost any program on a vulnerable server, programs that could allow the hacker to delete files, steal information, or just about anything really.
So why is this bug so serious? For starters, 60% of all web servers have the bug – a much higher rate than the Heartbleed bug because Bash is more integral to these servers – it’s such a basic part of the system, and such an old part of it, that nobody though it could possibly be buggy … until now. It also appears that OS X is vulnerable, although most OS X installs are not configured to allow attacks from outside. Most worryingly, it’s not just web servers that can be affected – any device running some version of Linux and has Internet access *could be* affected, including smartphones, routers, even things like Blu-ray players and in-car entertainment systems. Many of these Internet-of-things devices are also difficult/impossible to update in order to fix the vulnerability, and as there are so many of these devices and so many versions of them, even the manufacturers (if they still exist) probably won’t know which devices/versions are/aren’t vulnerable. To make matters worse, the first set of patches that went out to various server versions were incomplete, giving admins a false sense of security if they didn’t notice that there were subsequent updates.
So basically, it’s a bug that’s very commonly found, easy to exploit, can potentially do a huge amount of damage and hard to fix for some devices – so yep, very serious.
So why is this bug not as serious as some in the media are reporting it to be? While there are probably billions of devices that run some variant of Unix/Linux, not all of them include Bash. Embedded devices such as routers prefer the lightweight BusyBox, which uses ash and not Bash, for example. So luckily iOS*, Android* and a lot of devices aren’t vulnerable to the bug, but that still leaves maybe a few hundred millions devices that are still vulnerable. But even if these devices are vulnerable, it takes a combination of different things (web accessible script that uses Bash to change environment variables) for something malicious to be done, and so while a few hundred million devices may have this bug, a much smaller number can actually be exploited successfully.
* Rooted devices that may have had Bash installed, may be vulnerable.
Hope that clears up a few things. Sorry for spending so much time on this, but it’s not as if I have a lot of other things to write about this week, as you’ll find out below.
![]()
A follow-up to a story from a few weeks ago (edit: it was actually last week … jeez, I have no sense of time these days), Google has hit back in the war (of open letters) between itself and Rupert Murdoch’s News Corp. News Corp labeled the search engine a “platform for piracy”, and Google has now hit back with its own open letter titled Dear Rupert and cites all of the company’s herculean efforts in fighting the piracy problem (222 million web pages removed from Google’s indexes, for example). It’s almost a line-by-line debunking of all the claims made in the now infamous News Corp letter, well worth a read if you want Google’s take on the whole “is Google taking over the world a good thing or not” debate.
![]()
I probably watch more Netflix than the average person, mainly because I like having certain shows on in the background while I’m working on the computer at home (yes it’s distracting, but in a good way!). I’ve already streamed through The Office twice this way, and I’m currently doing The Fresh Prince of Bel-Air via Mexican Netflix (as they have all the seasons). So the news that the average Netflix subscriber now watches 1.5 hours of content every day didn’t really strike me as surprising – I watch that much between lunch and afternoon tea.

You too can influence how Netflix decides what movies to add to their library (Not Intended to Be a Factual Statement)
But if you actually analyse what people are actually watching, I think you’ll find it’s more The Nanny, than The Wolf of Wall Street or any other high profile movie releases. This is because most top movies are simply not available on Netflix. New research shows that only 16% of popular and acclaimed films are actually on Netflix at the moment, compared to 94% on sell-through platforms like iTunes.
The latter, 94%, has been used by the MPAA to suggest that availability is not a huge issue when it comes to causes for piracy, but in reality, it’s the former 16% that may still be fueling the desire to download. It would be interesting to see what the piracy rate is for movies that do make it to Netflix, compared to movies that have never been on the platform – surely this should provide us with more valuable insight than simply saying “94%”.
Speaking of Netflix, I may have found a way to influence how Netflix decides which flicks to add to their library. For the past few months, whenever I have the time, I’ve been doing a search on Netflix for the delightful Martin Short, Nick Nolte comedy Three Fugitives. I know it isn’t there, but I’m searching for it anyway in the hope that the data boffins at Netflix spots the numerous searches being made for the movie and something gets done. And it’s worked! The movie will be available to stream in early October, thanks to my efforts and my efforts only I can only assume (as I must be the only one to be searching for this movie on Netflix, or the Internet in general). A similar thing happened with Harry and the Hendersons, which I had been furious searching for in the preceding months, and finally watched again on Mexican (or was that Canadian) Netflix this month. So get busy and start searching (obviously a trick that works better for titles that has little commercial value, then say searching for ‘Guardians of the Galaxy’).
Please note that the above advice contains zero scientific or logical merit, and is solely based on the flimsiest of empirical evidence, if you can even call it that.
![]()
And finally in gaming (and semi-copyright) news, Steam’s re-design of its web store now more prominently shows the DRM employed by the game (if any). A move that will surely be welcomed by gamers, tired of spending a sizable amount of money on a game, only to find it infected with DRM nonsense. A new notification is now shown on the right hand side of the game’s page, with a clear “warning: this is something that you probably won’t like” yellow background to make the DRM warning stand-out. Perhaps this will further discourage publishers from putting in bad DRM, because if we all start treating DRM just as something detrimental, such as a bad review or incompatibility problems, then maybe publishers will have less incentive to include them in the future.
——
Alright, that’s it for this week. See you in seven!